Audit Logging via Firehose
Audit logs and access logs are critical tools for enterprises, providing visibility into system activities, enhancing security, ensuring compliance, and supporting operational efficiency. They are useful for:
- Security and Threat Detection
- Compliance and Legal Protection
- Operational Efficiency and Troubleshooting
- Accountability and Fraud Prevention
- Forensic Analysis and Incident Response
Palisade keeps track of audit logs, allowing you to configure an endpoint where to receive a copy.
How it works
Customer configures an IAM role and a firehose endpoint in Organization settings. During the upload, the following environment specific IAM roles assume the customer configured IAM roles in order to perform PutRecordBatch on the configured firehose endpoint.
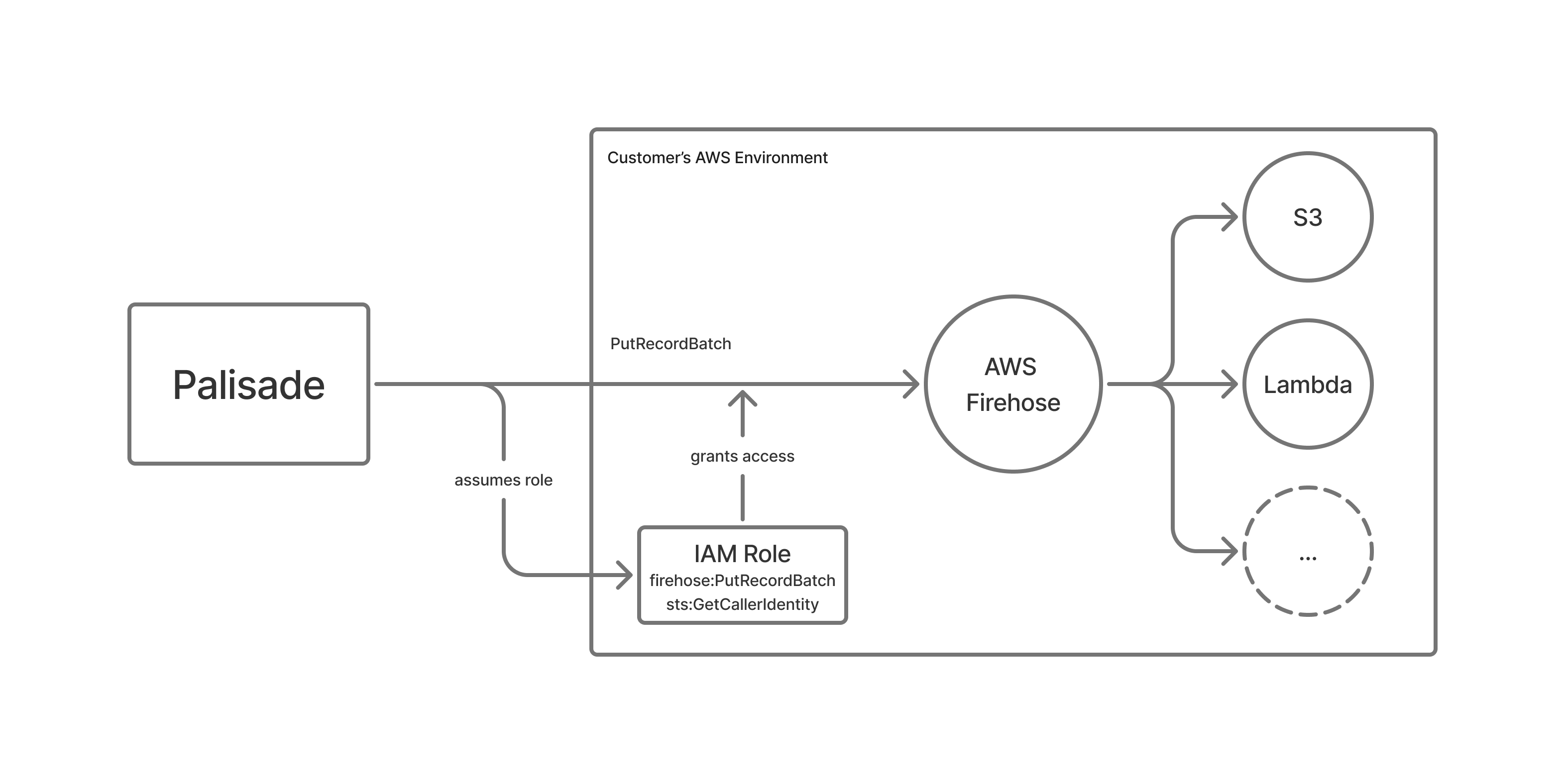
Once configured, Palisade will buffer and upload logs in batch every 15 seconds.
IAM Role
The IAM role that grants access to Palisade to upload logs to AWS Firehose must have following policies:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowFirehosePutRecordBatch",
"Effect": "Allow",
"Action": "firehose:PutRecordBatch",
"Resource": "arn:aws:firehose:REGION:ACCOUNT_ID:deliverystream/STREAM_NAME"
},
{
"Sid": "AllowStsGetCallerIdentity",
"Effect": "Allow",
"Action": "sts:GetCallerIdentity",
"Resource": "*"
}
]
}Additionally, in order to allow Palisade to assume this role, it must have the following IAM trust relationship:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowPalisadeAssumeRole",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::PALISADE_ACCOUNT_ID:PALISADE_IAM_RESOURCE_NAME"
},
"Action": "sts:AssumeRole"
}
]
}
Please contact Palisade support to get your respectivePALISADE_ACCOUNT_IDandPALISADE_IAM_RESOURCE_NAME
Log structure
Example log object received by AWS Firehose:
{
"id": 21119,
"orgId": "dac59f97-5984-4298-bebd-92c94b6184b4",
"type": 1,
"userId": "c1e08d96-07a3-4561-846f-dd5a5c274e29",
"deviceId": null,
"requestId": "2aa53531-2124-4501-b9bb-2ed8208ff0e8",
"jsonData": "eyJ1cmwiOiAiL3YyL2JhbGFuY2VzIiwgIm1ldGhvZCI6ICJHRVQiLCAiaGVhZGVycyI6IHsiQWNjZXB0IjogImFwcGxpY2F0aW9uL2pzb24sIHRleHQvcGxhaW4sICovKiIsICJPcmlnaW4iOiAiaHR0cHM6Ly9hcHAuZGV2ZWxvcG1lbnQucGFsaXNhZGUuY28iLCAiUmVmZXJlciI6ICJodHRwczovL2FwcC5kZXZlbG9wbWVudC5wYWxpc2FkZS5jby8iLCAiUHJpb3JpdHkiOiAidT0xLCBpIiwgIlNlYy1DaC1VYSI6ICJcIkNocm9taXVtXCI7dj1cIjEzNlwiLCBcIkdvb2dsZSBDaHJvbWVcIjt2PVwiMTM2XCIsIFwiTm90LkEvQnJhbmRcIjt2PVwiOTlcIiIsICJVc2VyLUFnZW50IjogIk1vemlsbGEvNS4wIChNYWNpbnRvc2g7IEludGVsIE1hYyBPUyBYIDEwXzE1XzcpIEFwcGxlV2ViS2l0LzUzNy4zNiAoS0hUTUwsIGxpa2UgR2Vja28pIENocm9tZS8xMzYuMC4wLjAgU2FmYXJpLzUzNy4zNiIsICJYLVJlcXVlc3QtSWQiOiAiMmFhNTM1MzEtMjEyNC00NTAxLWI5YmItMmVkODIwOGZmMGU4IiwgIlNlYy1GZXRjaC1EZXN0IjogImVtcHR5IiwgIlNlYy1GZXRjaC1Nb2RlIjogImNvcnMiLCAiU2VjLUZldGNoLVNpdGUiOiAic2FtZS1zaXRlIiwgIkFjY2VwdC1FbmNvZGluZyI6ICJnemlwLCBkZWZsYXRlLCBiciwgenN0ZCIsICJBY2NlcHQtTGFuZ3VhZ2UiOiAiZW4tR0IsZW4tVVM7cT0wLjksZW47cT0wLjgiLCAiWC1BbXpuLVRyYWNlLUlkIjogIlJvb3Q9MS02ODMwOWI0Yy0zYTcyZWZjNDI0NGQ2ZDEzNjQ5OThmY2IiLCAiWC1Gb3J3YXJkZWQtRm9yIjogIjgwLjEuMjUzLjI0NSwxMC4wLjYuNDMiLCAiU2VjLUNoLVVhLU1vYmlsZSI6ICI/MCIsICJYLUZvcndhcmRlZC1Qb3J0IjogIjQ0MyIsICJYLUZvcndhcmRlZC1Qcm90byI6ICJodHRwcyIsICJBdXRob3JpemF0aW9uLUhhc2giOiAiNTE5ZGY0ZjdhYmUxODlkOWY3ODkxYzIyZDEyMGQ2NTQiLCAiU2VjLUNoLVVhLVBsYXRmb3JtIjogIlwibWFjT1NcIiIsICJYLUVudm95LUF0dGVtcHQtQ291bnQiOiAiMSIsICJYLUZvcndhcmRlZC1DbGllbnQtQ2VydCI6ICJCeT1zcGlmZmU6Ly9jbHVzdGVyLmxvY2FsL25zL2dhdGV3YXkvc2EvYXBpLWdhdGV3YXk7SGFzaD05NDUwNjdiYjMzNWMwZjEwOTYyZjNmYmFkZWJhOGQ4ZTE3ZGM1YWQ4MmI2ZWExYWZjZTAzNDdiZGU5N2ZmOTYwO1N1YmplY3Q9XCJcIjtVUkk9c3BpZmZlOi8vY2x1c3Rlci5sb2NhbC9ucy9pc3Rpby1zeXN0ZW0vc2EvaXN0aW8taW5ncmVzc2dhdGV3YXkiLCAiWC1FbnZveS1FeHRlcm5hbC1BZGRyZXNzIjogIjEwLjAuNi40MyJ9LCAicmVxdWVzdCI6IHsiYm9keSI6ICIifSwgInJlc3BvbnNlIjogeyJib2R5TGVuZ3RoIjogNjIsICJzdGF0dXNDb2RlIjogMjAwfSwgImR1cmF0aW9uTXMiOiAzLCAicmVtb3RlQWRkciI6ICI4MC4xLjI1My4yNDUifQ==",
"source": "api-gateway",
"receivedAt": "2025-05-23T15:59:08.764753Z",
"createdAt": "2025-05-23T15:59:08.757472Z"
}The orgId attribute is guranteed to be non-nil and correspond to the customer's organization ID. The userId, deviceId and requestId may provide further information regarding the initiator of the request but they are not guaranteed to be present.
The property jsonData has the following internal JSON structure when base64 decoded:
{
"url": "/v2/users/info",
"method": "GET",
"headers": {
"Accept": "application/json, text/plain, */*",
"Origin": "https://app.palisade.co",
"Referer": "https://app.palisade.co/",
"Priority": "u=1, i",
"Sec-Ch-Ua": "\"Chromium\";v=\"136\", \"Google Chrome\";v=\"136\", \"Not.A/Brand\";v=\"99\"",
"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36",
"X-Request-Id": "e630143f-1df1-4116-966d-b1819d62683f",
"Sec-Fetch-Dest": "empty",
"Sec-Fetch-Mode": "cors",
"Sec-Fetch-Site": "same-site",
"Accept-Encoding": "gzip, deflate, br, zstd",
"Accept-Language": "en-GB,en-US;q=0.9,en;q=0.8",
"X-Amzn-Trace-Id": "Root=1-6835a5e2-5291d44c2c702d3165875983",
"X-Forwarded-For": "80.1.253.245,10.0.6.43",
"Sec-Ch-Ua-Mobile": "?0",
"X-Forwarded-Port": "443",
"X-Forwarded-Proto": "https",
"Authorization-Hash": "37f53fd9408cf4920708dbc5731acace",
"Sec-Ch-Ua-Platform": "\"macOS\"",
"X-Envoy-Attempt-Count": "1",
"X-Forwarded-Client-Cert": "By=spiffe://cluster.local/ns/gateway/sa/api-gateway;Hash=4a74148afabd7bc011d206439ef2a2acdb2f4db3fce0a17097b4d65b1982b70a;Subject=\"\";URI=spiffe://cluster.local/ns/istio-system/sa/istio-ingressgateway",
"X-Envoy-External-Address": "10.0.6.43"
},
"request": {
"body": ""
},
"response": {
"bodyLength": 199,
"statusCode": 200
},
"durationMs": 5,
"remoteAddr": "80.1.253.245"
}Limitations
- Support for AWS Firehose only
- Logs are buffered for 15 seconds before sending to firehose
